Cybersecurity

Protect yourself and your business
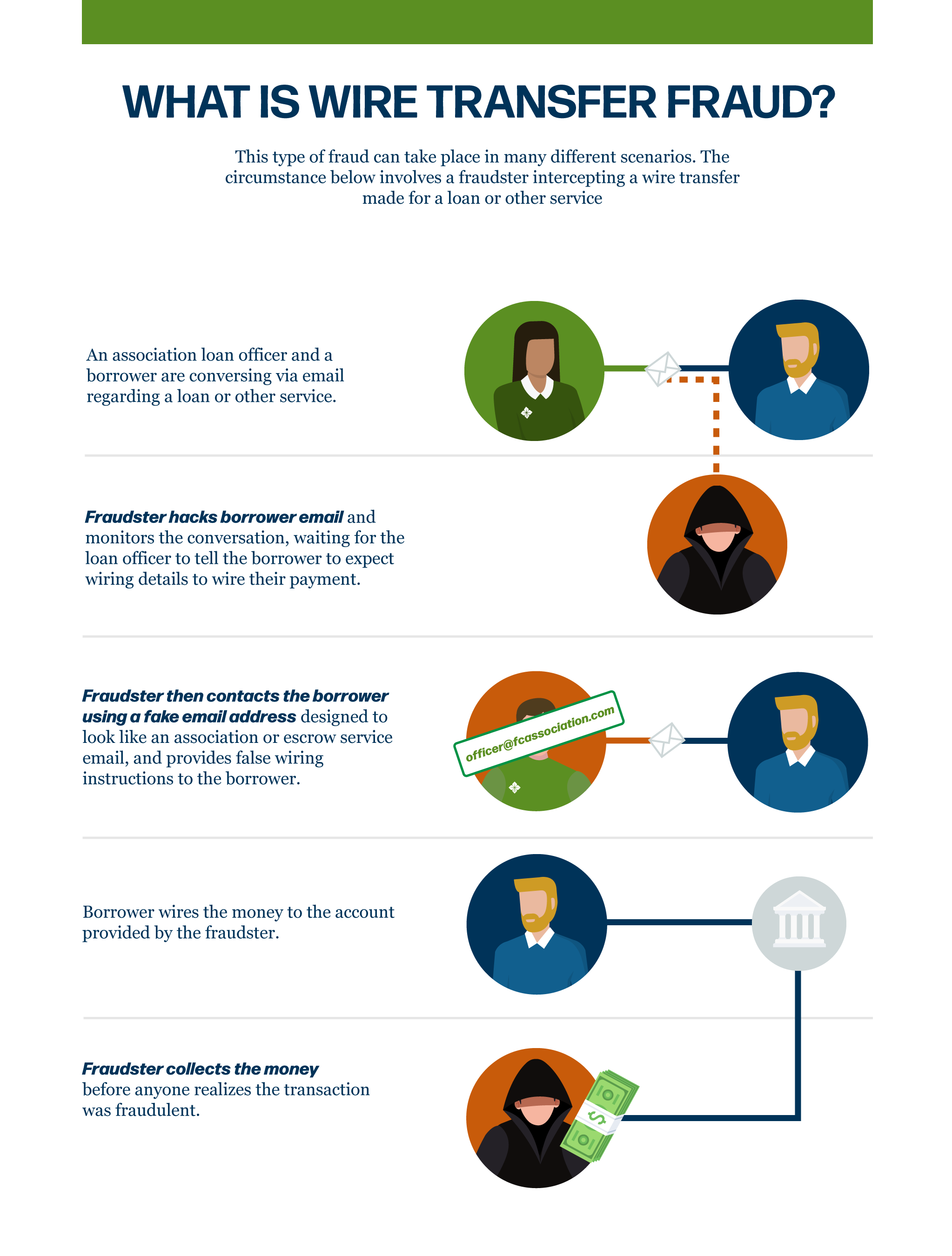
Arming yourself with knowledge on how cybercriminals operate — and the tricks they have up their sleeves — is the best defense against cyberattacks for your household or business.
What are three simple measures you can take to protect your information from these malicious cyberattackers?
Protect yourself and your business
Arming yourself with knowledge on how cybercriminals operate — and the tricks they have up their sleeves — is the best defense against cyberattacks for your household or business.
What are three simple measures you can take to protect your information from these malicious cyberattackers?

Identify and avoid scam emails, texts and calls that seek to steal your money
Secure and update your devices so they cannot be hijacked
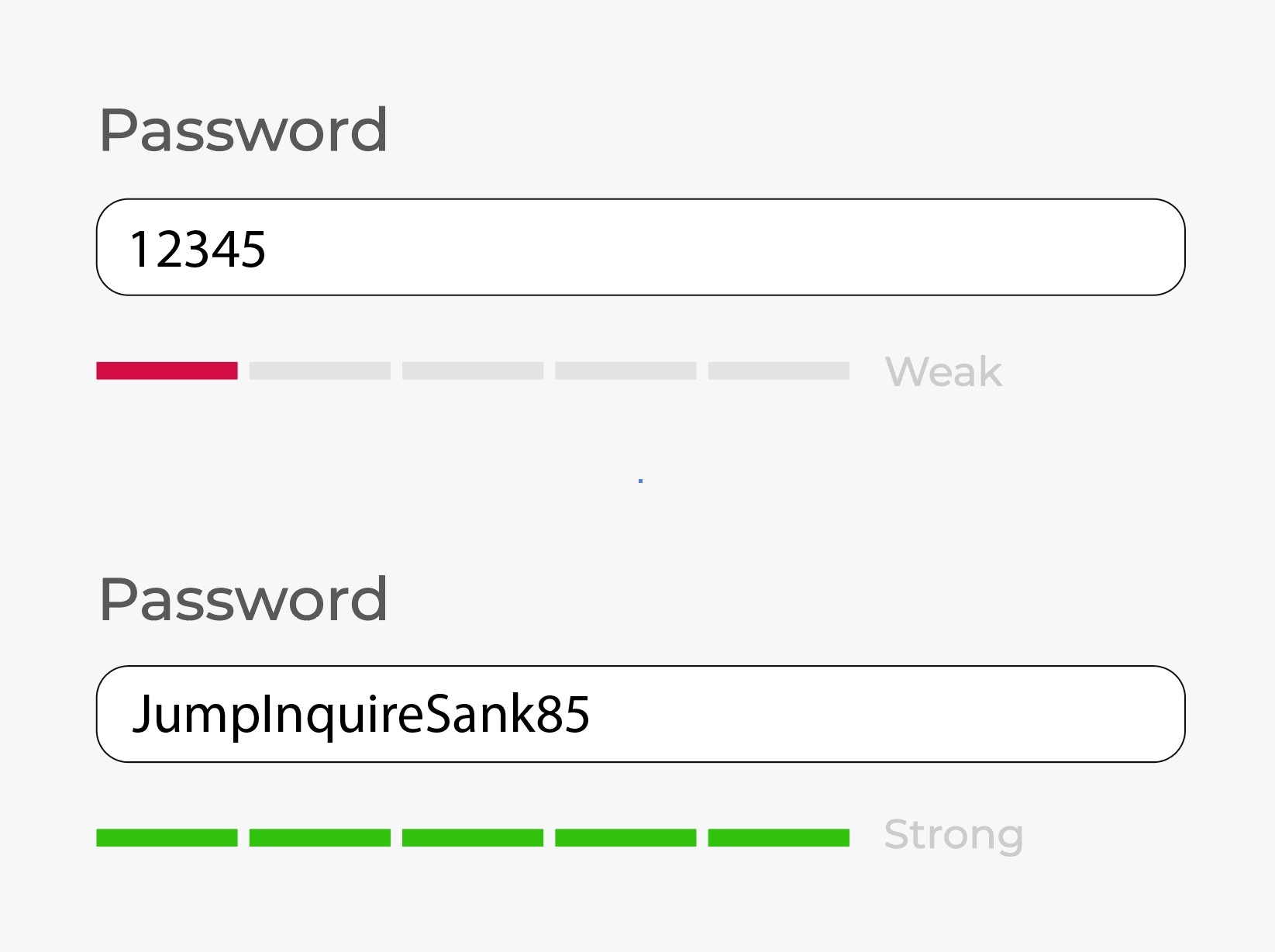
Use hard-to-guess passwords to stop accounts from being hijacked